DDoS-Angriffe
-
ALLGEMEIN

Radware mit neuen High-End-Plattformen zur Abwehr von Angriffen
Radware stellt unter der Bezeichnung DefensePro X eine leistungsstarke neue Serie von sechs -Abwehrplattformen gegen Cyberangriffe vor.
Weiterlesen ... -
ALLGEMEIN
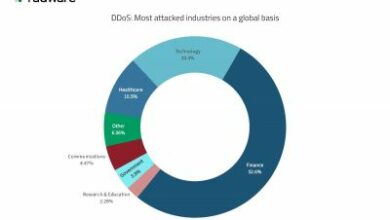
Radware Bericht für 2022: Bösartige DDoS-Angriffe steigen um 150%
Radware hat seinen Global Threat Analysis Report 2022 veröffentlicht.
Weiterlesen ...
